Websites
Compromised or malicious websites represent one of the various avenues through which viruses can infiltrate your computers.
Downloads
Downloading external documents from vendors or clients’ Dropbox, G Drive, OneDrive, and other file-sharing platforms poses a risk of introducing viruses into your network.
Sabotage
A growing trend among hackers involves extracting information, either willingly or unwillingly, from employees or former employees to gain unauthorized access to the firm’s computers and servers.
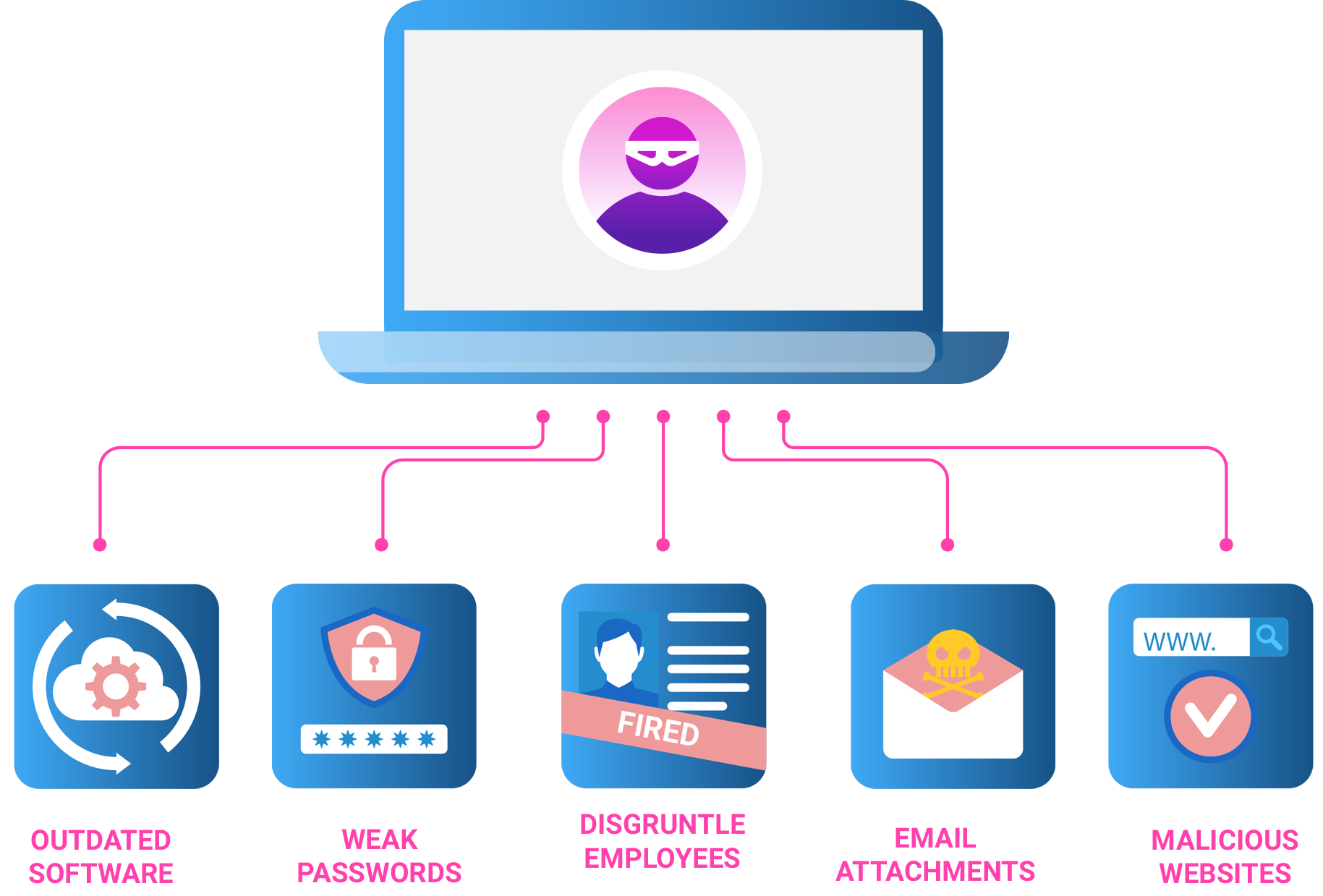
The Problem
Entry points
Virus entry points are pathways that allow malicious software to gain unauthorized access to computer systems and networks. These may include email attachments with malware, infected websites, malicious links, and compromised software or hardware.
Social engineering tactics, like phishing emails or deceptive online content, exploit human vulnerabilities to trick users into unwittingly facilitating virus entry. Outdated software, unpatched security vulnerabilities, and insecure network configurations are common entry points that cyber attackers exploit.
Effectively securing and monitoring these potential entry points is crucial for robust cybersecurity. A comprehensive defense strategy requires a combination of technological solutions and user awareness to mitigate the risk of virus infiltration.

The Solution – Part 2
2b1 Care Advanced Security + EDR
Advanced Security + EDR is a comprehensive cybersecurity solution that merges advanced endpoint protection with Endpoint Detection and Response (EDR) capabilities. This integrated solution surpasses traditional antivirus methods by utilizing innovative technologies like behavioral analysis, machine learning, and heuristic analysis.
Beyond detecting known malware, Advanced Security + EDR proactively identifies and responds to emerging threats in real time. This robust cybersecurity suite ensures endpoint protection through a potent blend of preventive measures and swift response capabilities, safeguarding digital assets in an ever-changing threat landscape.


Why do i need it
Hackers are more sophisticated

While browsing, several clients landed on websites containing malicious code, triggering a 2b1 Care Advanced Security + EDR response. This resulted in alerts being sent out, and we were able to track the specific computer, user, browser, and visited website with minimal effort.
Paolo Broggi – CEO
Build cyber resilience against ransomware attacks
Time to upgrade your security software to the next level and stay a step ahead of hackers with enterprise grade, anti virus, crypto virus, crypto mining protection and EDR.

